11-22, 15:15–16:00 (Europe/Vienna), Track 2
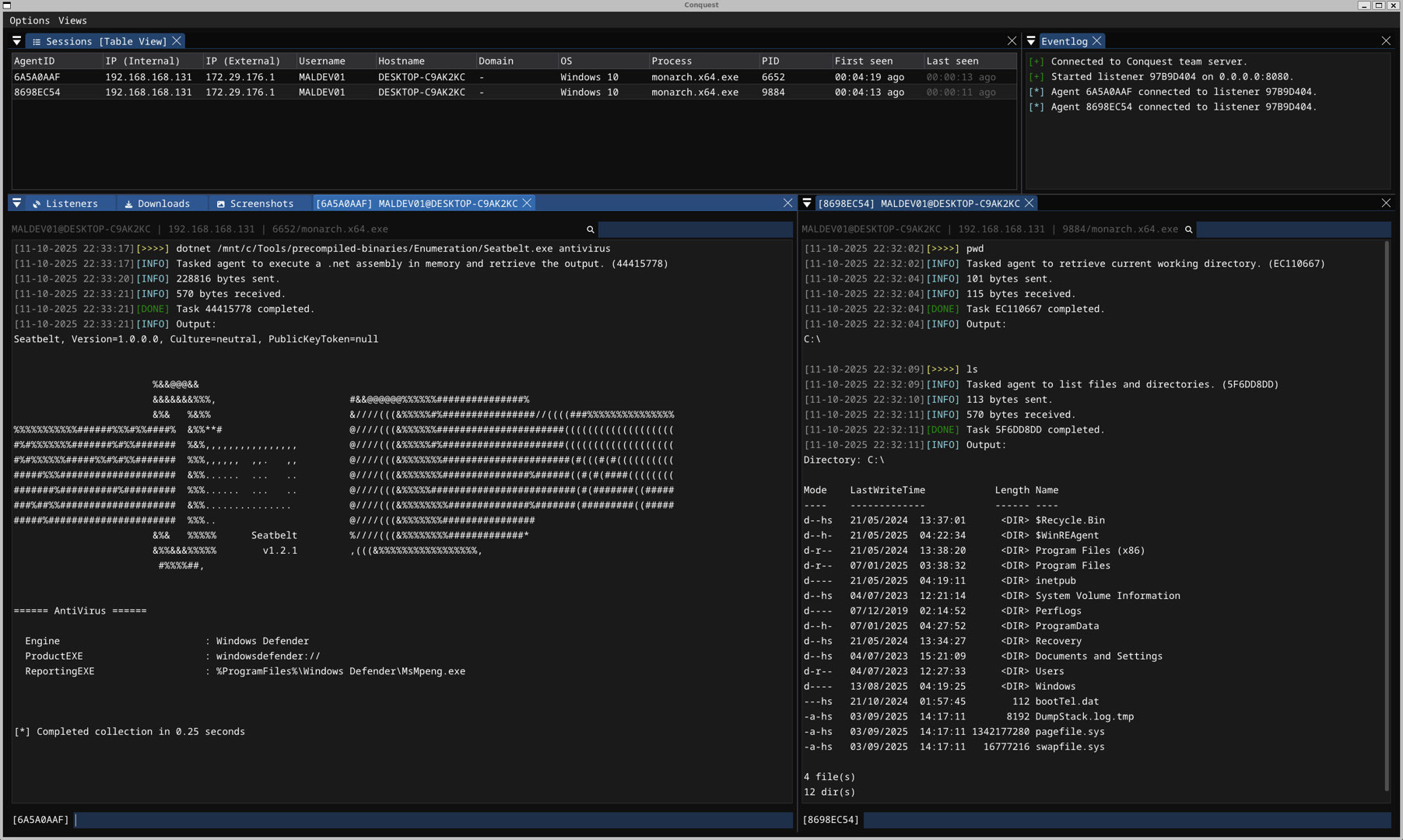
Command and Control (C2) frameworks are indispensable in modern red teaming and penetration testing. They enable operators to execute post-exploitation tooling, maintain access to compromised systems, all while keeping track of executed commands and their outputs. For the past couple of months, I have been working on developing a C2 framework from scratch using the Nim programming language, and have since implemented core features, such as secure C2 traffic encryption, a malleable C2 profile system, sleep obfuscation and many more.
C2 frameworks are highly complex pieces of software, consisting of multiple architectural layers, components and features. At the bare minimum, modern C2s have at least a client and server component, as well as some sort of agent/implant/payload. The server handles connections and requests from agents that are executed on target systems, allowing operators to - as the name suggests - command and control them remotely from a client user interface.
In addition to front- and backend development, data management and a lot of difficult design decisions, C2 developers are required to balance functionality with operational security and configurability, so that their programs can be easily customized or extended to slip past security controls or the watchful eyes of blue teamers.
In this talk, I want to take you on a journey of how I turned the idea and vision of building a custom command and control framework into reality. I will cover the up’s and down’s, the successes and failures, the reality checks and the rewarding lessons learned that come with such a project, all with the goal of answering the question: Should or should you not try to build your own C2?
Agenda:
- What are Command & Control frameworks? How do they work?
- Design choices: Language, Architecture, Communication
- Framework features and how to implement them (Beaconing, C2 profiles, Sleep obfuscation, Modules, Evasion and more)
- Risk, Reward & Lessons Learned: Why should(n’t) you build a C2?
Conquest: https://github.com/jakobfriedl/conquest/
Jakob is a penetration tester and security professional from Austria. He is particularly passionate about offensive security, including network penetration testing and Windows malware development. By day he works in an internal penetration testing team, conducting and leading engagements, while at night he keeps up-to-date with new attack techniques or works on his security-focused blog.